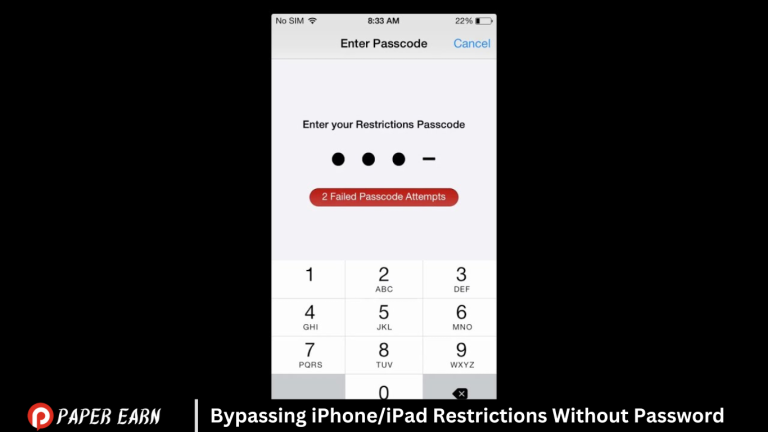
Attempting to bypass iPhone/iPad restrictions without the password may violate terms of service and could potentially cause permanent damage to your device. It’s always recommended to seek official support from Apple or consult with a certified technician. Engaging in unauthorized access can lead to legal repercussions and jeopardize your device’s security. It’s best to prioritize privacy and security by following proper protocols and seeking legitimate solutions.
Introduction to iPhone/iPad Restrictions
iPhone/iPad Restrictions, also known as Parental Controls, are features designed to limit and control access to certain apps, content, and features on iOS devices. They serve multiple purposes, including managing children’s device usage, preventing access to inappropriate content, and safeguarding device settings.
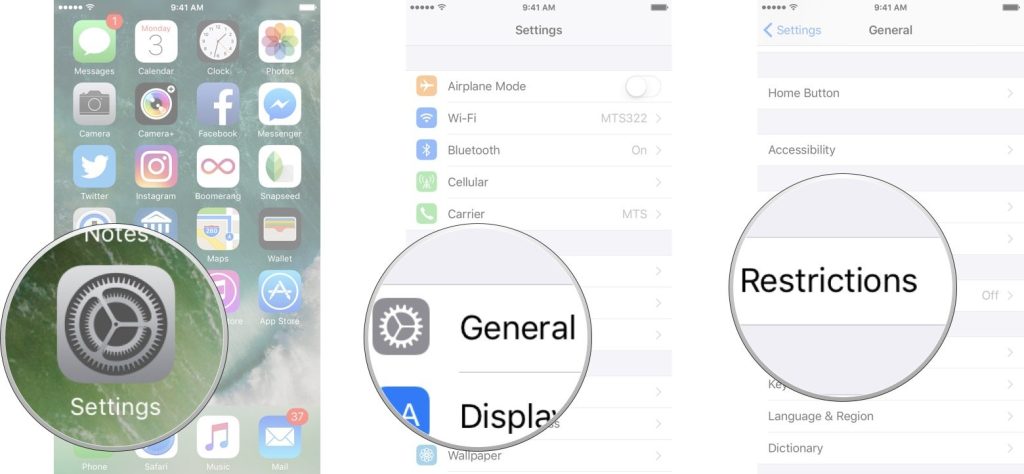
Understanding the Password Protection
Password protection is a security measure to safeguard digital accounts and data. Users create unique passwords, typically a combination of letters, numbers, and symbols, which grant access to their accounts. Strong passwords are essential, as they are harder to guess or crack. Additionally, employing techniques like multi-factor authentication adds an extra layer of security. Regularly updating passwords and avoiding common phrases or easily guessable information further enhances protection against unauthorized access.
Risks and Legal Considerations
Risks associated with password protection include unauthorized access to sensitive information, potential data breaches, and identity theft. Legal considerations include compliance with data protection laws such as GDPR or HIPAA, which mandate the secure handling of personal information. Failure to implement adequate security measures may result in legal penalties, financial losses, damage to reputation, and loss of trust from customers or users.

Precautions and Ethical Considerations
Precautions in password protection involve educating users on creating strong, unique passwords, implementing multi-factor authentication, and regularly updating security measures. Ethical considerations include respecting user privacy, transparently handling and storing passwords, and promptly disclosing any breaches or vulnerabilities. Upholding ethical standards ensures trust between users and service providers, fostering a secure online environment while respecting individuals’ rights and autonomy.
Alternatives to Bypassing Restrictions
When faced with restrictions on an iPhone or iPad without the password, consider alternative approaches before resorting to bypassing methods:
- Contact Apple Support: Reach out to Apple’s customer support for assistance. They may provide guidance or options for resolving the issue without bypassing restrictions.
- Resetting Device Settings: If you have access to the device settings, consider resetting them to default. This may remove any restrictions that were previously set.
- Consulting with the Device Owner: If you’re not the owner of the device, communicate with them to understand the reason behind the restrictions. They might be willing to provide the password or adjust the settings as needed.
- Using iCloud for Device Management: Employ iCloud’s management features to remotely manage and adjust settings on the device if enabled.
- Restoring from Backup: If you have a backup of the device, restoring it to a previous state may remove the restrictions.
- Seeking Professional Assistance: In cases where restrictions are causing significant issues, consider seeking assistance from a professional technician or Apple Authorized Service Provider.
Utilizing Third-Party Software
Utilizing third-party software can offer solutions to various needs, but it comes with considerations. Users should assess the reputation, security, and terms of service of the software provider to ensure compatibility with their goals and legal requirements. Additionally, reliance on third-party software may entail dependencies, potential vulnerabilities, and risks of data breaches. Regular updates, monitoring, and adherence to best practices mitigate these risks.
Risks of Data Loss and Device Damage
Data loss risks encompass accidental deletion, hardware failure, malware, or cyberattacks. Damage to devices can result from physical mishandling, electrical issues, or environmental factors like water or heat. Mitigation involves regular backups, both local and cloud-based, to safeguard against data loss. Employing antivirus software, and firewalls, and practicing safe browsing habits help protect devices from damage and mitigate the risk of data loss due to malware or cyber threats.
Prioritizing Privacy and Security
Prioritizing privacy and security involves implementing robust measures to protect sensitive information and mitigate risks. This includes encryption for data transmission and storage, implementing access controls, and regularly updating security protocols. Respect for user privacy entails transparent data handling practices, obtaining consent for data collection, and adhering to relevant regulations such as GDPR or CCPA. Prioritizing privacy and security fosters trust and integrity in digital interactions.
Frequently Asked Questions
Is it possible to bypass iPhone/iPad restrictions without a password?
Yes, some methods claim to bypass restrictions, but they often require technical expertise and may not be reliable or legal.
Are there legitimate ways to bypass restrictions without a password?
No, Apple maintains strict security measures to prevent unauthorized access to devices and their features.
Can jailbreaking bypass restrictions without a password?
Jailbreaking can circumvent some restrictions, but it’s not recommended due to security risks, voided warranties, and potential legal issues.
What are the risks of attempting to bypass restrictions without a password?
Risks include device damage, loss of data, security vulnerabilities, and potential legal consequences for violating terms of service or laws.
Are there legal implications for bypassing restrictions without a password?
Yes, bypassing restrictions without authorization may violate Apple’s terms of service and could lead to legal action.
Can I seek help from Apple Support to bypass restrictions without a password?
No, Apple does not provide assistance or support for bypassing security measures.
Do third-party tools claim to bypass restrictions without a password?
Yes, but the efficacy and legitimacy of these tools vary, and their use may breach terms of service or laws.
Can restoring my device to factory settings bypass restrictions without a password?
Restoring a device erases its data and settings, which may remove restrictions, but it also deletes all personal information and requires setting up the device again.
Is there a way to bypass restrictions without a password if I forgot it?
Apple provides methods for resetting forgotten passwords, but they require verifying identity and may involve data loss.
How can I prevent unauthorized access to my device?
Secure your device with a strong password, Touch ID, or Face ID, enable Find My iPhone/iPad, and avoid sharing your password with others. Regularly update your device’s software to patch security vulnerabilities.
Conclusion
Bypassing iPhone/iPad restrictions without a password is a complex and risky endeavor. While there may be methods and tools claiming to offer solutions, they often come with significant drawbacks, including potential legal consequences and security risks. It’s essential to prioritize the security and integrity of your device and data by adhering to Apple’s recommended practices, such as using strong passwords, enabling security features like Touch ID or Face ID, and regularly updating your device’s software. Remember that protecting your privacy and security is paramount in today’s digital age.